Four days.
That’s the average amount of time school networks are down after a cyberattack. Recovery takes even longer—around 30 days—according to a report from Comparitech.
Cyberattacks against US schools are deeply disruptive and expensive. According to the same report, ransomware attacks against colleges and K-12 districts cost educational institutions $3.56 billion in downtime alone and impacted over 950,00 students.
The number of reported cyberattacks against K-12 has increased dramatically since 2016.
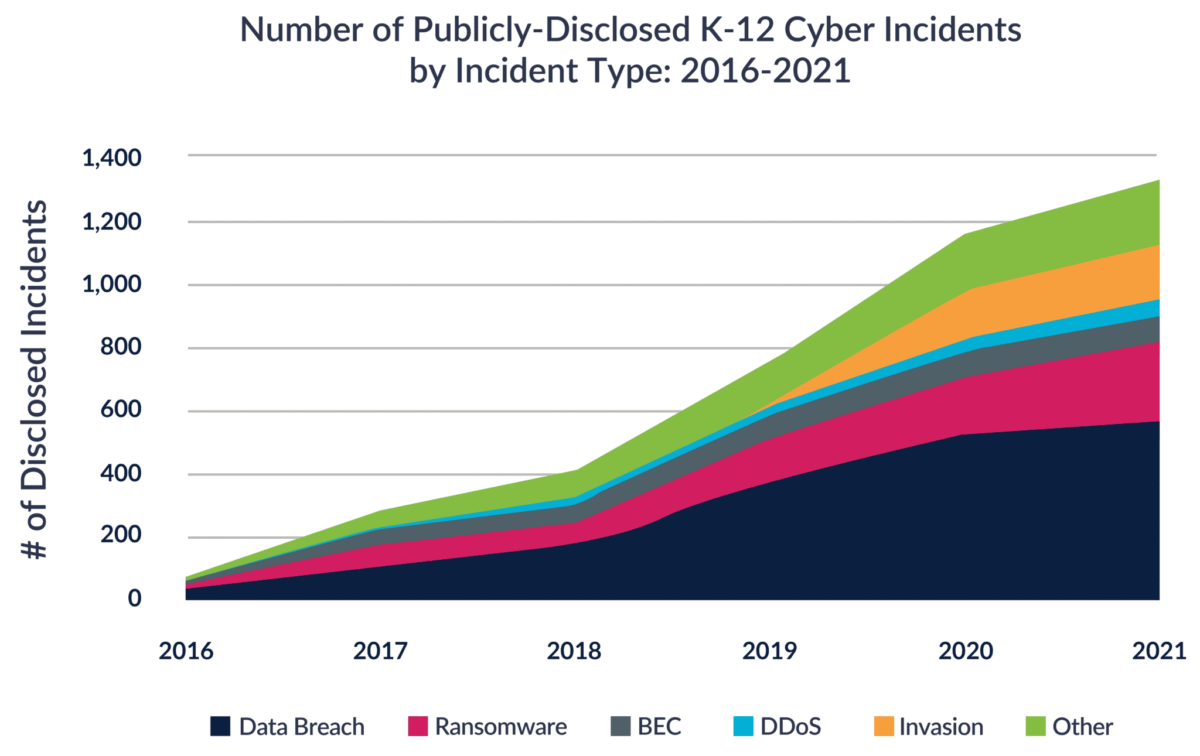
Cybercriminals are targeting districts with increasingly sophisticated cyberattacks designed to steal money and data. Districts must do everything they can to prevent cyberattacks. To better understand what districts are up against, we’ll examine three common ways schools are cyberattacked and how they can protect themselves and their students’ data.
1. Malware attacks
Malware is one of the most dangerous types of cyberattacks because it can be hard to spot quickly. Often, schools encounter malware as a virus that attacks student devices to gain information or cause harm to district networks.
The most well-known type of malware is ransomware—where a district’s network data is hijacked and held hostage until a ransom is paid. In the absence of payment, hackers may publish students’ private data. Several such attacks against districts have received widespread media attention.
What can K-12 districts do to protect themselves from malware attacks?
School devices, malicious links or websites, and outdated software can all serve as entry points for malware.
Districts need to ensure they have strong firewalls at the network and application levels to help stop malware from infiltrating a district’s network. Additionally, the district’s web filter can be an effective tool. For instance, Lightspeed Filter™ offers security features that help categorize and block malware.
Next, districts should create and maintain a malware playbook with the steps they will take if a malware attack occurs. The malware playbook should include a contact list (such as a district’s insurance carrier and even the local FBI contact) and address the district’s communication plan, detailing who will need to be notified and what information will be shared should an attack occur. It is important to test the playbook, so districts should run a gameday around it.
In the case of a successful malware attack, seek immediate professional help. Malware can be very serious and fighting it requires a strong understanding of cybersecurity and security systems. The solution here is not to deal with it individually unless you are a professional.
2. Denial of service attacks
Denial of Service (DDoS) attacks account for roughly half of all cybercrimes committed against schools. During a DDoS attack, a school’s website or network will be purposefully inundated with requests. This causes all network communication, both in- and outbound, to freeze.
These attacks can be conducted by third parties for a nominal fee, making DDoS attacks a low barrier to entry for anyone (even a student) looking to keep a school from going about its business.
What can K-12 districts do to protect themselves from DDoS attacks?
Robust firewalls can help identify incoming attacks, notify administrators, and block the damage.
To mitigate the fallout of a DDoS attack, create backup sites and systems that can handle redirected web traffic, known as network redundancy. This helps districts keep running if their primary systems go down.
Cloudflare is a possible solution as well, depending on your district’s website. If your district’s website is hosted in a cloud provider, the provider likely already offers some protection.
3. Breaches of student and staff data
Schools are responsible for vast amounts of data about their students, including:
- Names
- Addresses
- Social Security numbers
- Grades
- Disciplinary records
- Medical information
Data breaches are a broadly defined type of cybercrime that describes when any such personal data is accessed and obtained by someone not authorized to have it.
For students, this type of data theft can have serious consequences that last into their adult lives. And because district networks don’t only have access to student information, the personal information about staff members is also always at risk.
What can K-12 districts do to protect themselves from data breaches?
According to a report by Kindergarten Through Twelfth Grade Security Information Exchange (K12 SIX), the most common access point for data breaches at schools is through third-party vendors and administrative services. Lax agreements with third-party vendors can leave confidential information exposed to unauthorized users or lead to instances of physical data misappropriation.
To mitigate this risk and protect student data, school districts need to ensure the partners and vendors they work with use up-to-date, comprehensive security features. Edtech tools like Lightspeed Analytics™ can help districts with this by quickly diagnosing and flagging applications vulnerable to student data privacy violations.
Additional steps school districts can take to prevent cyberattacks
Breaches in cybersecurity are most likely to occur due to human error. While this could be caused by careless behavior, it is more likely the person has a poor understanding of cybersecurity as a process.
“We humans remain the weak link in cybersecurity,” said John Genter, the VP of Security & Cloud Operations at Lightspeed Systems®. “I find people are generally worried they must be cybersecurity experts. I believe it’s important we help people understand their role is to be cybersecurity aware, not cybersecurity experts. This is something anyone can do.”
Regular cybersecurity training is a district’s best defense against human error. District staff needs to be educated about the danger of security breaches, the typical threats, and the ways to prevent them.
To help prevent cyberattacks, besides prioritizing cybersecurity training, K-12 districts must:
- Keep all systems updated. That’s the number one thing districts can do to prevent cyberattacks. Patching is critical.
- Conduct an annual audit of the district’s network and security features, including any patches or updates that need to be made and any gaps in the security performance of third-party applications and vendors. To help run a successful audit, consider getting analytics software like Lightspeed Analytics to easily aggregate the data needed for an audit.
- Make digital citizenship a part of the curriculum for all staff and students. Practicing digital citizenship not only helps prevent cyberbullying and harassment, but also helps people understand their digital footprint, safe online communication, and online privacy.
These are some of the ways to protect your district from cyberattacks. To learn more, download our free guide How to Protect Your K-12 District from Cyberattacks.

